s偷
参考https://juejin.cn/post/6844904098328739853
官方提供hook 模板https://frida.re/docs/examples/android/
hook输入框https://www.jianshu.com/p/82d2bfeb4fbf
获取输入框
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| import frida, sys
def on_message(message, data):
if message['type'] == 'send':
print("[*] {0}".format(message['payload']))
else:
print(message)
jscode = """
Java.perform(() => {
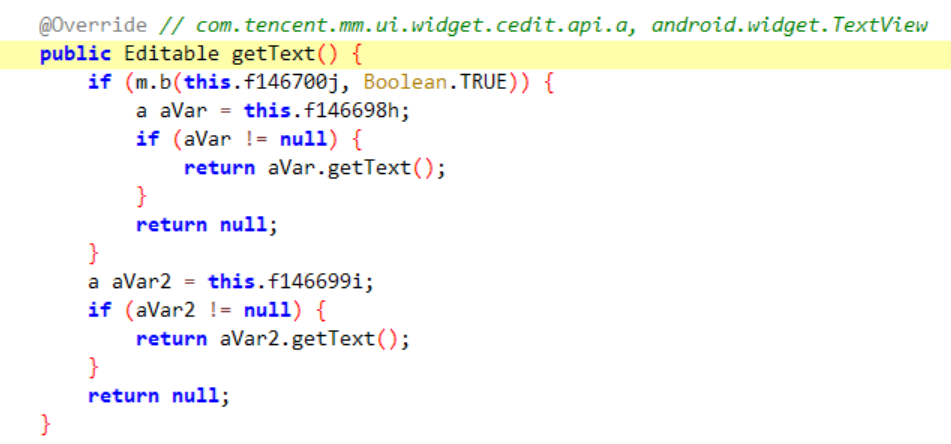
let MMFlexEditText = Java.use("com.tencent.mm.ui.widget.cedit.api.MMFlexEditText");
var CharSequence = Java.use("java.lang.CharSequence");
MMFlexEditText["getText"].implementation = function () {
console.log(`MMFlexEditText.getText is called`);
let result = this["getText"]();
var resultStr = Java.cast(result, CharSequence);
console.log(`MMFlexEditText.getText result=${resultStr}`);
return result;
};
});
"""
process = frida.get_usb_device().attach('微信')
script = process.create_script(jscode)
script.on('message', on_message)
print('[*] Running CTF')
script.load()
sys.stdin.read()
|
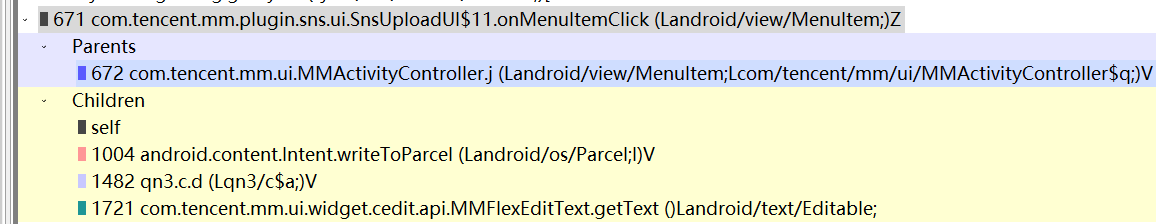
创建发起动态 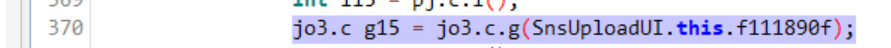
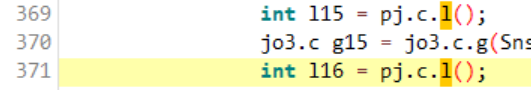
两个pj.c.l是在输入法展开时进行,返回值恒为4000
访问量
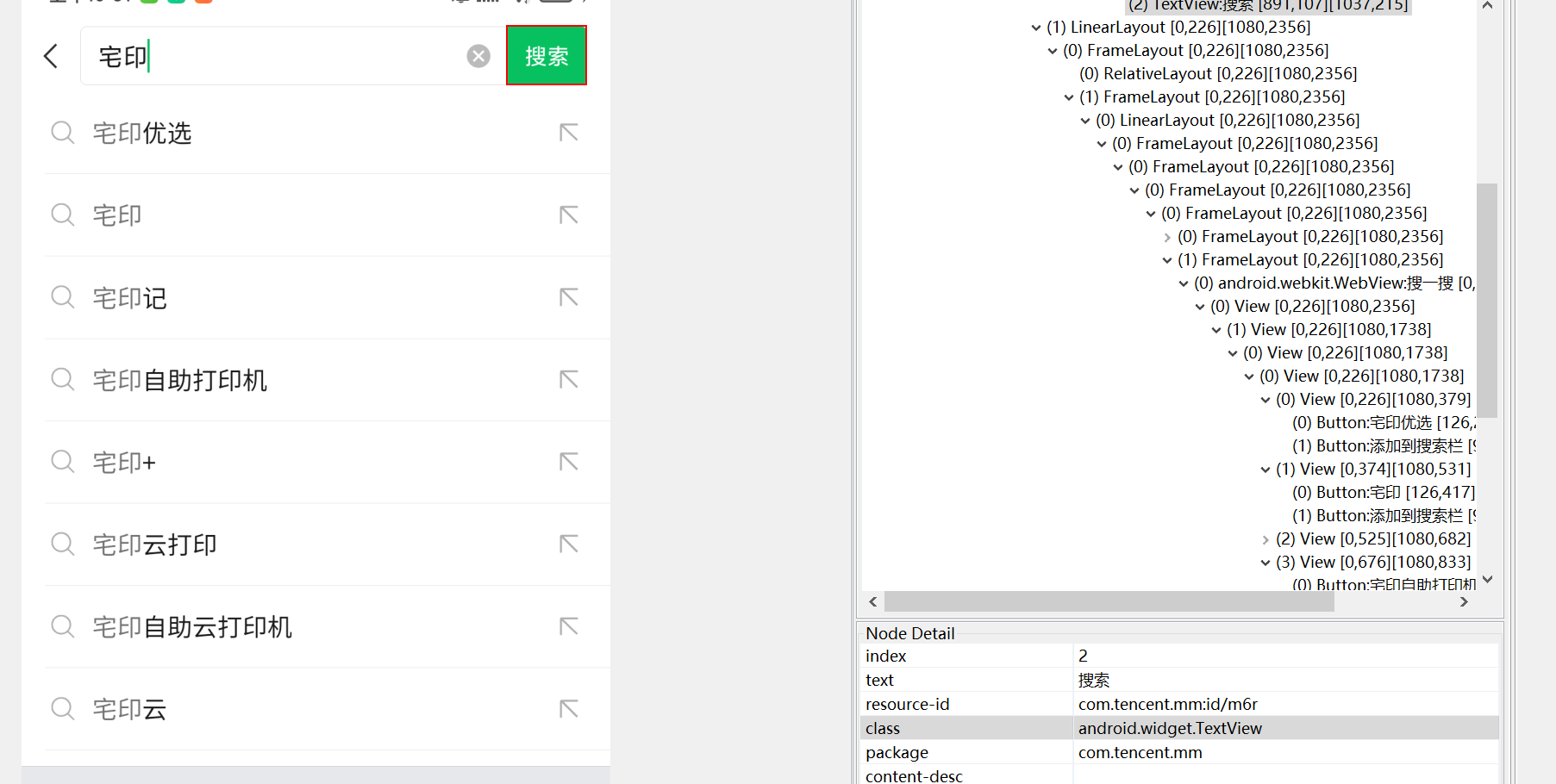
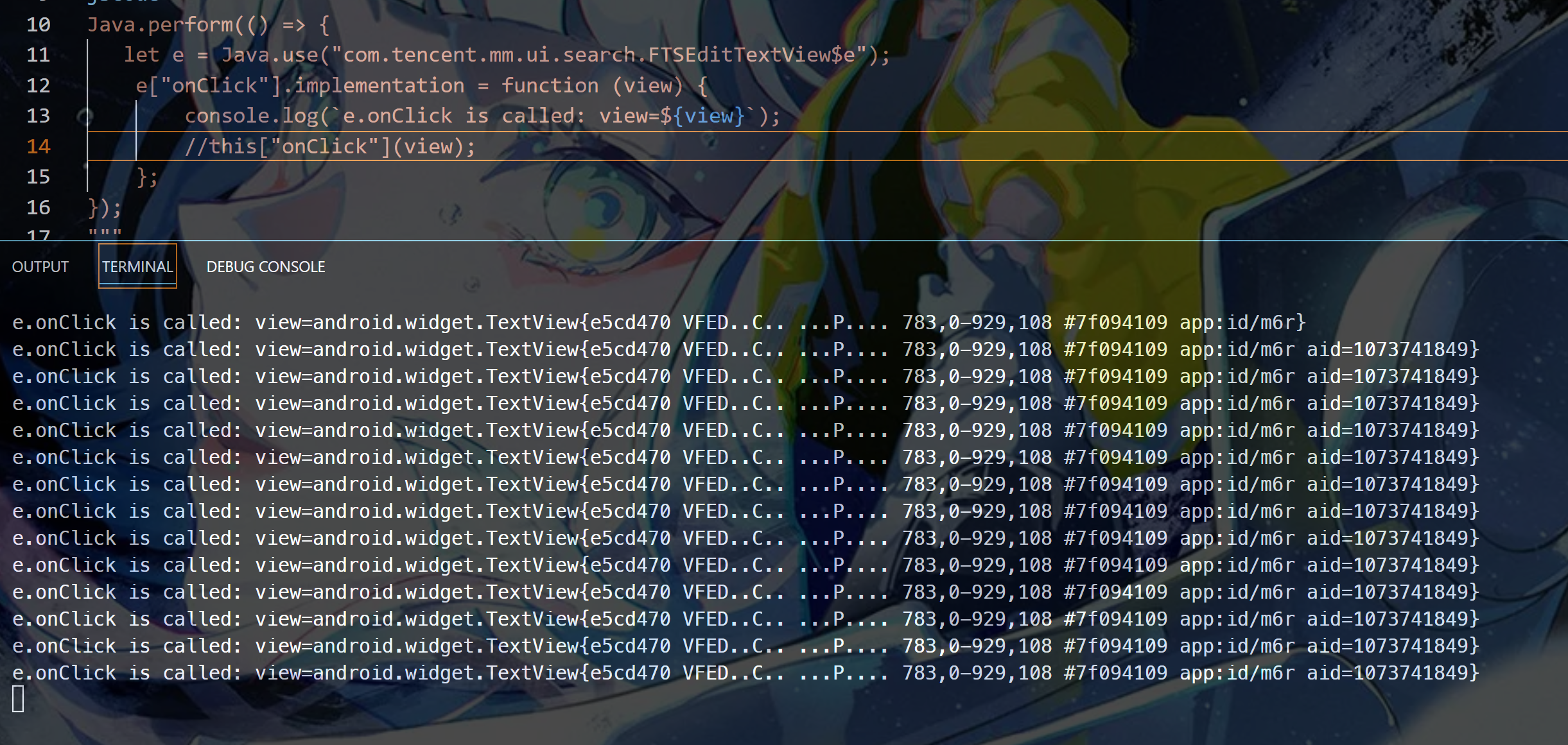
class: android.widget.TextView
resource-id: com.tencent.mm:id/m6r
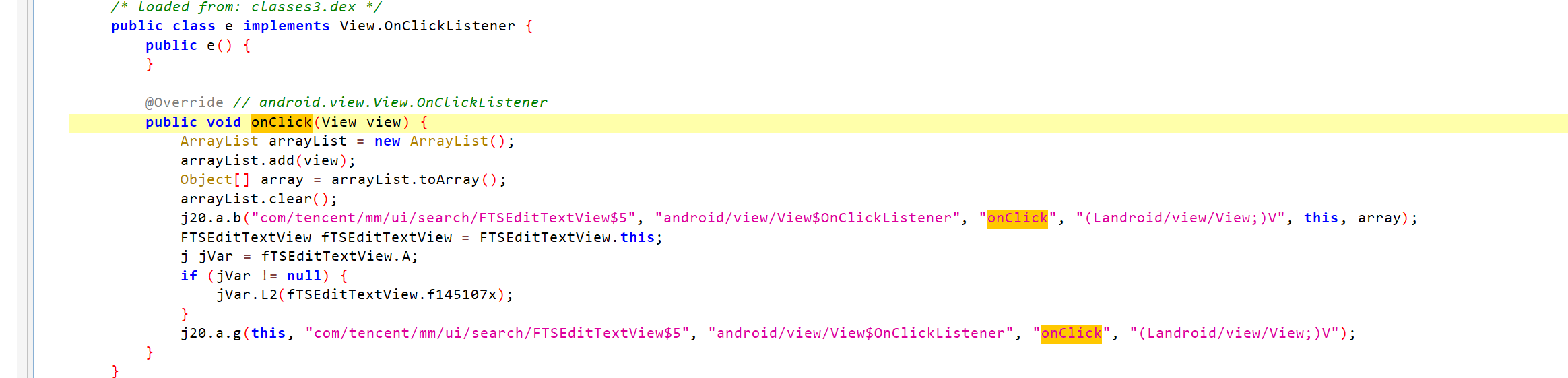
搜索框类:com.tencent.mm.ui.search.FTSEditTextView.e